Data Privacy Day
Garden State Cyber Threat Highlight
Original Release Date: 1/28/2021
Thursday, January 28, 2021 is Data Privacy Day! Data Privacy Day is a global effort to empower individuals and encourage businesses to respect privacy, safeguard data, and enable trust. Every year, a single day is dedicated to recognizing the importance of data privacy and being informed about how information is being used, collected, or shared in our digital culture. We discuss privacy protections, valuable data and data privacy, and recommendations to keep you and your data safe year round.
Privacy Protections
Privacy is a fundamental human right and is known as the freedom from unauthorized intrusion or unauthorized disclosure of information about an individual. Organizations can create and implement privacy policies to protect personally identifiable information (PII) that they collect, store, and transmit. They are advised to conduct privacy impact assessments to determine privacy risk to individuals; provide effective privacy notices; limit the collection, access, sharing, and retention of PII; confirm the integrity of PII; and implement privacy awareness and training.
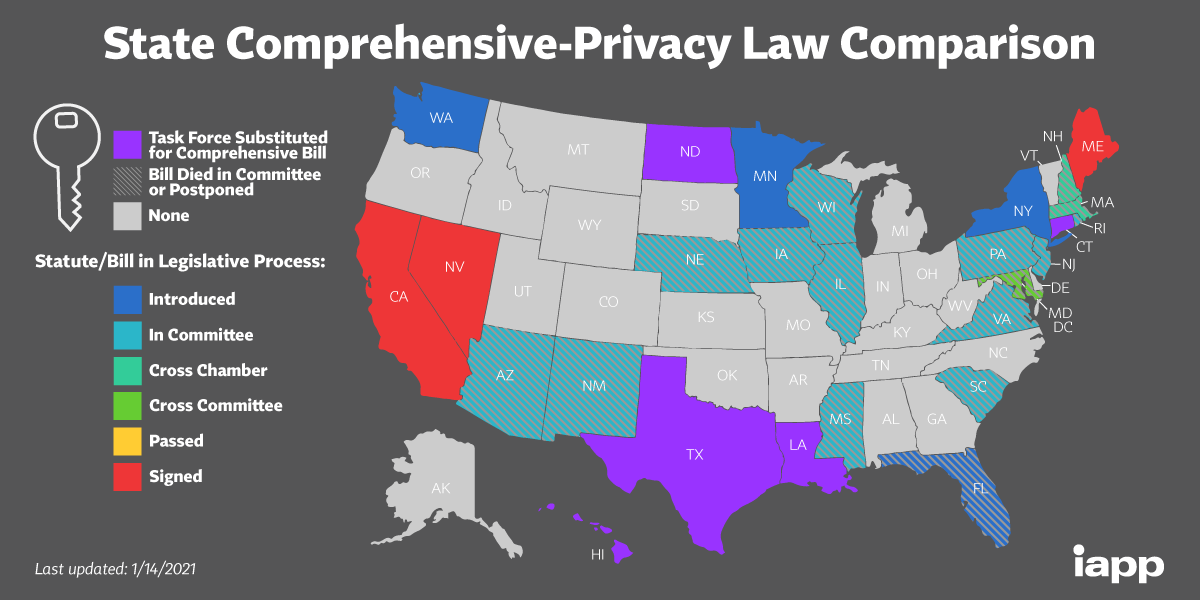
Privacy law refers to the laws that deal with the regulation, storage, and use of data— such as PII, personal health information (PHI), and financial information of individuals—which can be collected by governments, public or private organizations, or other individuals. These laws consider an individual’s privacy rights and/or reasonable expectation of privacy. The European Union’s General Data Protection Regulation (GDPR) has improved data privacy and the overall risk posture for organizations, and it has prepared organizations in the US and other countries for compliance with data privacy regulations. Although there is no comprehensive US federal-level general consumer data privacy law, data privacy legislation has been passed in the US after GDPR, including laws in California, Maine, and Nevada. Other states, including New Jersey, have started the data privacy legislative process, as evident in the privacy law comparison map.
Valuable Data and Data Privacy
Data is defined as a subset of information in an electronic format that allows it to be stored, retrieved, or transmitted. The following data is considered valuable:
- Personally identifiable information (PII) is defined as any information about an individual, including:
(1) Any information that can be used to distinguish or trace an individual's identity, such as name, Social Security number, date and place of birth, mother's maiden name, or biometric records; and
(2) Any other information that is linked or linkable to an individual, such as medical, educational, financial, and employment information. - Personal health information (PHI) includes all individually identifiable health information, including demographic data, medical diagnoses and histories, test results, insurance information, and other information used to identify a patient or provide healthcare services or coverage. The HIPAA Privacy Rule places limitations on the uses and disclosures of PHI. PHI includes 18 identifiers, such as patient names, addresses, dates related to the individual, phone numbers, email addresses, and Social Security numbers. If the identifiers are removed, the information is considered to be de-identified PHI and, therefore, is not subjected to the HIPAA Privacy Rule restrictions.
- Criminal justice information (CJI) includes the protection of private or sensitive information gathered by local, state, and federal law enforcement agencies. Examples of CJI are fingerprints, criminal background information, copies of private documents, and other information classified as sensitive. The Criminal Justice Information Services (CJIS) Security Policy provides the appropriate controls to protect the full lifecycle of CJI—from creation through dissemination—whether at rest or in transit.
- Student educational records are defined as a range of information about a student that is maintained in schools in any recorded way, such as handwriting, print, computer media, video or audio tape, film, microfilm, and microfiche. Examples of educational records are personal information, such as student identification codes, Social Security numbers, and pictures; grades, test scores, and courses taken; disciplinary records; special education records; medical and health records created, collected, or maintained by the school; and documentation of attendance, schools attended, and degrees earned. The Family Educational Rights and Privacy Act (FERPA) protects the privacy of both paper and computerized student education records, guarantees parent review and appeal, restricts disclosure of student records, and other provisions.
- Intellectual property (IP) is defined as creations of the mind, such as inventions, literary and artistic works, designs, and symbols, names and images used in commerce. Examples of IP are copyrights, patents, trademarks, industrial designs, geographical indications, and trade secrets. Intellectual property law provides rules for securing and enforcing legal rights to IP, and it protects any product of the human intellect from the unauthorized use by others.
- Financial or payment card information is defined as cardholder data—primarily debit card and credit card information—that is stored, processed, and transmitted by organizations. The Payment Card Industry Security Standards Council developed the Payment Card Industry Data Security Standard (PCI DSS), which provides security standards for organizations of major card brands that handle cardholder data. These security standards keep systems and sensitive payment card information secure in order to reduce fraud.
Recommendations
In addition to privacy protections, there are proactive steps you can take to protect you and your data.
- Reduce your digital footprint. Minimize your online presence and PII exposure, and exercise caution when uploading sensitive PII or other information to websites, applications, or social media. The NJCCIC received reports of PII exposure on social media platforms. For example, someone was using a victim’s profile picture of their family in their own posts and spam messages. In another case, a threat actor impersonated a victim by creating multiple fake social media profiles to send harassing communications to their contacts in their contact list.
- Value and protect your information. Make informed decisions about sharing your data with certain individuals, businesses, services, and apps.
- Check and configure privacy and security settings. Check these settings to help manage your cyber risk and limit how and with whom you share information. Use the NJCCIC instructional guides for Android, Facebook, Google, Instagram, and Twitter, and configure similar settings on all other social media sites. Information on how to access privacy settings for additional popular devices and online services can be found on the National Cybersecurity Alliance webpage.
- Conduct frequent searches and remove personal data. Conduct searches for personal data and remove any tags for photos of you and your family on social media. Contact connections to remove personal data about you and your family. Utilize Michael Bazzell’s Extreme Privacy guide to remove personal data from the internet, which includes submitting opt-out/removal requests for public record or ‘people search’ websites where your information is readily accessible.
- Deactivate or delete accounts that are no longer in use. Deactivate or permanently delete any social media or online account that is no longer in use. Sites such as https://justdelete[.]me provide instruction on how to remove information and delete accounts for numerous online and social media sites.
- Monitor and report any suspicious activity. Monitor all personal and financial accounts (including banking and credit institutions) and report any suspicious activity or fraudulent charges immediately.
- Refrain from sharing or saving login credentials or other sensitive information. Login credentials and other sensitive information should not be shared with anyone. Avoid auto-saving passwords, payment card numbers, or contact information when prompted by your operating system, browser, website, or applications.
- Exercise caution with communications. Refrain from divulging personal or financial information via phone, text messaging, or email without verifying the requestor via a separate means of communication before taking any action.
- Change the default password. Default passwords for devices/accounts can be used to gain unauthorized access to systems and networks.
- Use unique, complex passwords for all devices/accounts. Unique passwords for each device/account prevents password reuse attacks, in which threat actors obtain your password for one account and use it to compromise an additional account using the same credentials.
- Enable multi-factor authentication (MFA) where available. MFA is the use of two or more factors to authenticate to an account or service. This significantly reduces the risk of account compromise via credential theft in which your password has been exposed. Although MFA is an additional step to authenticate, it is an important one—not only to protect an individual account, but also the community at large.
- Keep devices up to date. Stay informed about publicly-disclosed vulnerabilities and update devices—including firmware—to the latest version to ensure they are patched against known vulnerabilities that could be exploited by threat actors to gain unauthorized access to your device and/or data. If a device is unable to receive updates from the vendor, consider not purchasing or discontinuing use of the device.
- Secure physical devices. Safeguard devices and ensure a password/passcode is enabled for all devices to prevent unauthorized access in the event a device is lost or stolen.
Resources
- NJCCIC How Big is Your Footprint?
- NIST Guide to Protecting the Confidentiality of Personally Identifiable Information (PII)
- National Cybersecurity Alliance Data Privacy Day