Emotet Campaigns Return After Hiatus
NJCCIC Alert
Original Release Date: 7/23/2020
Summary
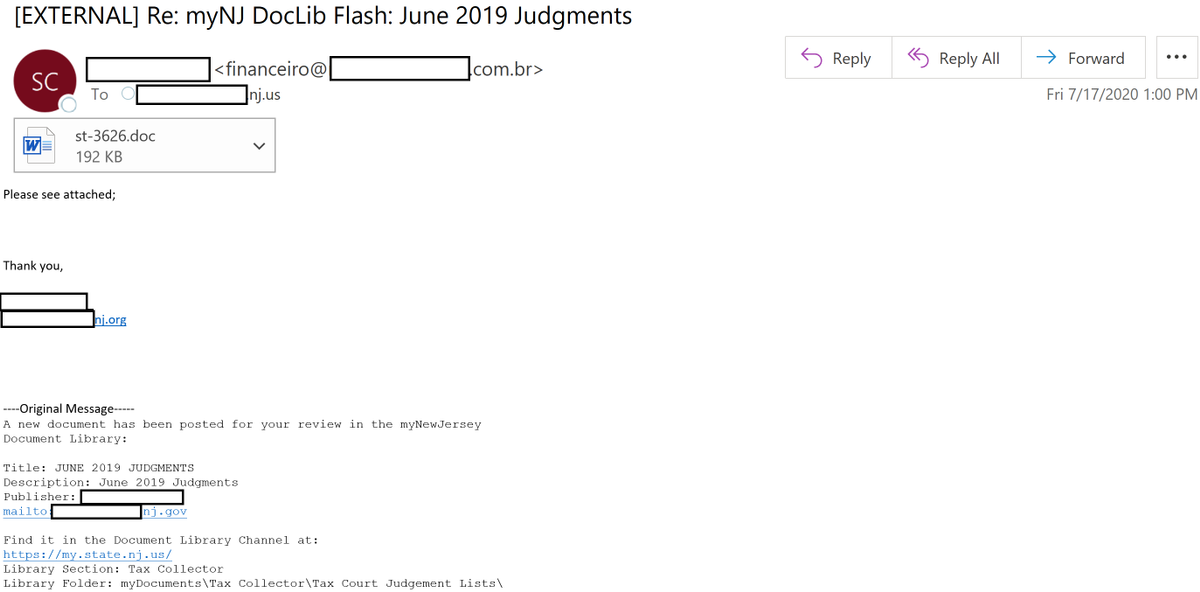
After a five-month hiatus, Emotet campaigns have resurged at an alarming rate. The NJCCIC has observed numerous attempts to deliver spam emails to NJ State employee inboxes, consistent with open-source reporting. Emotet , originally identified as a banking trojan, is often delivered via malicious attachments in phishing emails and has continuously evolved to become more dangerous and evasive with each new version. The trojan is known to target Windows devices to deliver additional malware and is capable of credential stealing, email harvesting, and spreading via local networks. It has also been involved in network compromises that ended in ransomware infections. Targets include organizations across North America and Europe, and activity is attributed to TA542, a Russian-speaking threat group. The most recent campaigns include Word documents or PDF attachments containing malicious macros that, if enabled, will download and install Emotet. Subject lines include payment remittances, invoices, or shipment updates, and often appear to be forwarded messages or part of an email reply chain. Additionally, one of the campaigns drops Qakbot, or Qbot, as a supplementary payload. At the time of this writing, four separate campaigns have been identified. One targeted phishing attempt sent to NJ state employees (above image) referenced June 2019 judgments and the myNewJersey portal.
Recommendations
The NJCCIC recommends users educate themselves and others on these continuing threats and tactics to reduce victimization. Users are advised to avoid clicking links or opening attachments delivered in emails from unknown senders, and exercise caution with emails from trusted senders. To verify an email’s legitimacy, contact the sender via a separate means of communication. Additionally, if infection is suspected/detected, administrators are urged to audit network logs and email accounts after removing the infected device(s) from the network to limit proliferation. Further details and Indicators of Compromise can be found in the MalwareBytes Labs blog post.