Impersonation Scams
Garden State Cyber Threat Highlight
Original Release Date: 3/4/2021
The first week in March is National Consumer Protection Week, which helps people understand their consumer rights, manage their money, protect their privacy, and avoid scams. Impersonation scams are one example of a scam in which threat actors spend time researching their target, pretend to be a trusted person or entity, and lure their victims with different and personalized social engineering tactics. They may also exploit current event themes such as taxes, unemployment, COVID-19 vaccines, and COVID-19 stimulus relief. They target victims to persuade them into sharing information, transferring money, and/or installing malware. The NJCCIC continues to observe and receive reports of impersonation scams and provides recommendations to educate users and organizations and reduce the likelihood of victimization.
Threat actors may impersonate trusted sources, such as family, friends, colleagues, and legitimate businesses and banks, including executives, vendors, and customers. They may also impersonate officials from government agencies—such as the Internal Revenue Service (IRS), Social Security Administration (SSA), and the Federal Bureau of Investigation (FBI). They attempt to convince their target to divulge sensitive information or perform an action, such as wiring funds.
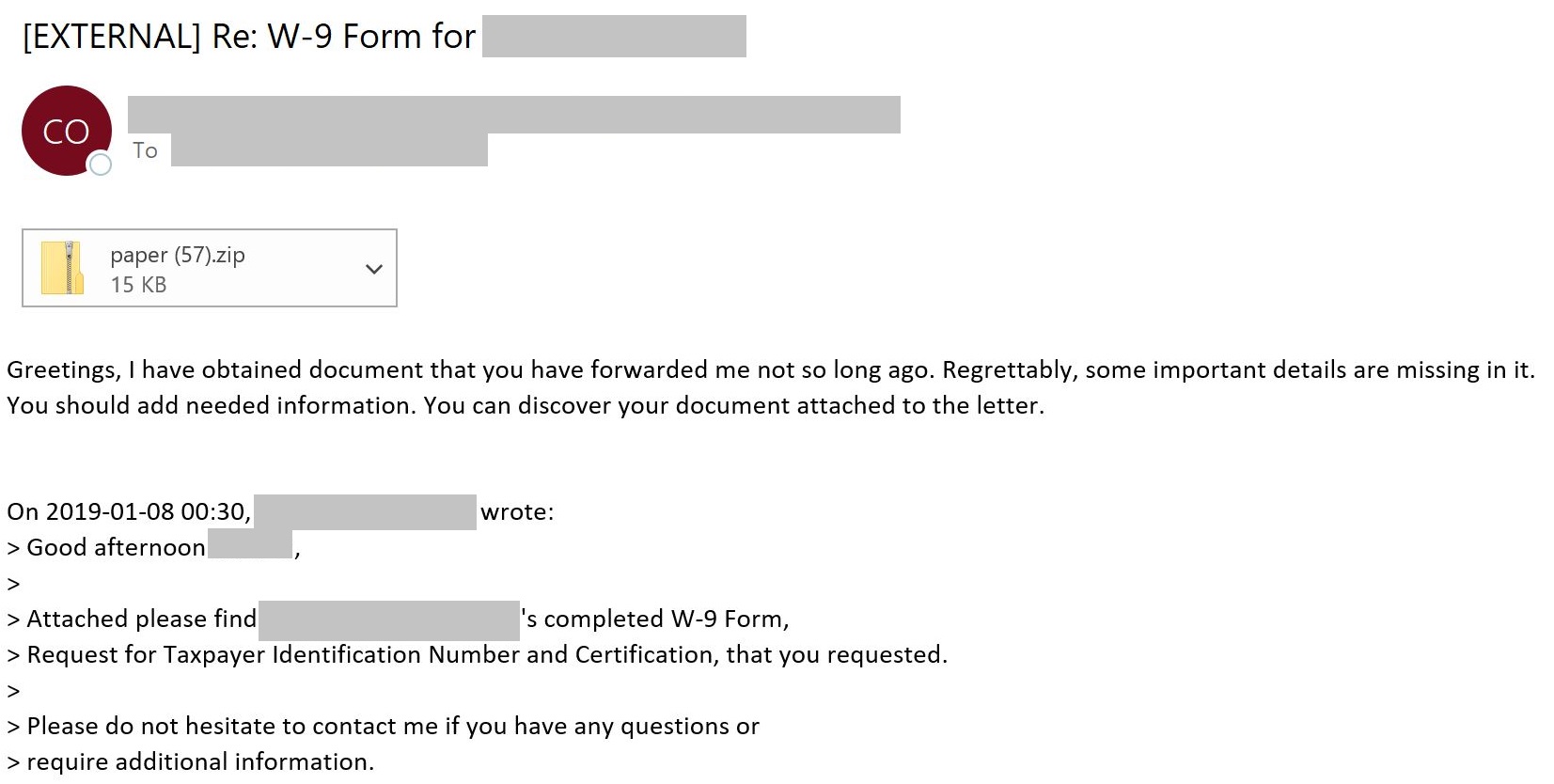
The NJCCIC observed multiple email campaigns attempting to be delivered to NJ State employees. These emails impersonate businesses and financial solutions, appear to be initial emails or replies to earlier email conversation threads, and have subject lines that reference business names, notifications, invoices, or forms. They include ZIP or XLS file attachments with a DocuSign theme and contain macros that, if enabled, download and install malware, such as Qbot, IcedID, and TrickBot. The attachment name may contain the word “paper,” “document,” “upload,” or “prepared.” In the example below, this impersonation email purportedly appears to be from a business replying to an earlier conversation thread. The subject line references a tax form for the sender’s business and the email contains the redacted sender’s email signature, including name, business name, address, phone number, and email address. The sender convinces the target to update information in a document in the attached paper(57).zip file. When the attachment is unzipped and opened, the contents of the Microsoft Excel file display “This Document is Protected” with a DocuSign logo and instructions to enabled macros.
The NJCCIC also received reports of impersonation scams posing as senior executives or employees of targeted businesses and organizations. The threat actors send unsolicited emails and use the actual name of the senior executive or employee in the display name and email signature to make it look like it is sent from them. Although the email itself appears legitimate, the threat actors spoof the email account by creating a fictitious email that resembles the actual name or email address, making it more difficult to identity the legitimacy of the email. They solicit information or convince the target to take an action, such as making purchases or performing tasks.
In addition, government agencies should use the .gov top-level domain for their official websites to reduce the success of impersonation scams, as the .gov domain requires validation to register. There are many government agencies, however, that utilize an alternative top-level domain, such as .com or .org, which makes them easier targets for impersonation scams. Anyone, including threat actors, could register similar-looking .com or .org domains to more convincingly impersonate a government agency and create spoofed email accounts and/or websites.
Recommendations
The NJCCIC recommends users practice good cyber hygiene to protect themselves from these types of scams and help prevent future victimization.
- Value and protect your information. Make informed decisions about sharing your information with certain individuals, businesses, services, and apps.
- Exercise caution with communications. Users who receive unexpected or unsolicited emails from known senders are advised to respond to communications coming from official business email accounts and to confirm the legitimacy of the message or request via a separate means of communication—such as telephone—before taking any action.
- Navigate directly to websites. Navigate directly to authentic or official websites by typing the legitimate URL into the browser instead of clicking on links in messages, and refrain from entering login credentials on websites visited via links delivered in messages.
- Use secure websites. When sharing personal or financial information, ensure you are using verified, secure, and encrypted websites.
- Reduce your digital footprint. Threat actors can search for and use information that is readily available on the internet, including researching organizations to gather information about employees, vendors, or customers. Refrain from posting sensitive information online. If possible, businesses are advised to minimize information posted on official websites, including organizational structures and online directories.
- Report email violations. Users who send unsolicited emails may violate account policies and/or terms of use and should be reported to the email provider.
- Refrain from sharing login credentials or other sensitive information. Login credentials and other sensitive information should not be shared with anyone.
- Update passwords immediately following a data breach or potential compromise. Use a resource, such as haveibeenpwned.com, to determine if your information, such as an account password, has been revealed in a public data breach. Change exposed passwords for every account that uses it to protect against account compromise.
- Use unique, complex passwords for all accounts. Unique passwords for each account prevent password reuse attacks, in which threat actors obtain your password for one account and use it to compromise an additional account using the same credentials.
- Enable multi-factor authentication (MFA) where available. MFA is the use of two or more factors to authenticate to an account or service. This significantly reduces the risk of account compromise via credential theft in which your password has been exposed. Even if a threat actor obtains a user’s username and password, they will be unable to access that user’s account without their second factor. The NJCCIC encourages users to choose authentication apps, hardware tokens, or biometrics as a second factor over SMS-based authentication due to the risk of SIM-swapping, though using any form of MFA is beneficial. The website TwoFactorAuth.org maintains a comprehensive list of websites that offer MFA.
- Keep devices up to date. Stay informed about publicly-disclosed vulnerabilities and update devices—including firmware—to the latest version to ensure they are patched against known vulnerabilities that could be exploited by threat actors to gain unauthorized access to your device and/or data. If a device is unable to receive updates from the vendor, consider not purchasing or discontinuing use of the device.
- Backup devices. Protect your information from malware, hardware failure, damage, loss, or theft by making multiple copies and storing them offline.
- Report suspicious activity.