July 2020 Email Threats Round Up
NJCCIC Alert
Original Release Date: 8/6/2020
Summary
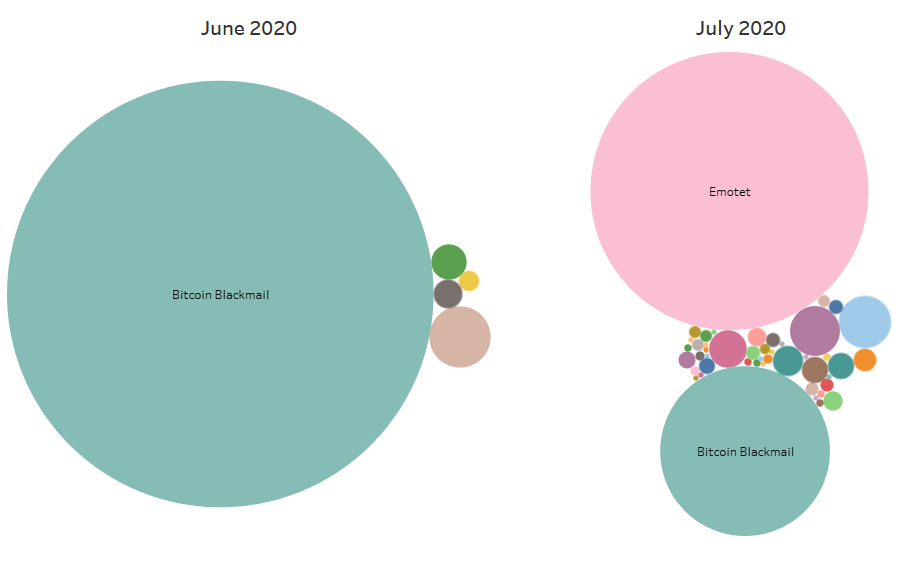
In the month of July, threat actors attempted to deliver malicious emails to NJ state employees through various campaigns. Most notably, there was a substantial increase in the amount of emails attempting to deliver Emotet, which the NJCCIC highlighted a few weeks ago and is evident in the comparison to top email threats from the month of June. Emotet is a trojan malware that began as a credential stealer and evolved into one of the most sophisticated and prevalent malware downloaders with many advanced capabilities. In the past couple of years, Emotet has been implicated in numerous ransomware attacks, particularly used in conjunction with the TrickBot trojan to deliver the Ryuk ransomware variant.
The NJCCIC advises users to avoid clicking links or opening attachments delivered in emails from unknown senders, and exercise caution with emails from trusted senders. To verify an email’s legitimacy, contact the sender via a separate means of communication. Additionally, if infection is detected, administrators are encouraged to re-image impacted systems.
One constant threat that continued to target state employees throughout the two months was Bitcoin Blackmail emails, also known as extortion or sextortion scams. These emails commonly reference one of the recipient’s passwords, likely taken from information revealed in a data breach, which adds a sense of legitimacy to the threat. The scammer claims to have accessed their device and recorded them visiting adult content websites, threatening to release that video to the recipient’s contacts if an extortion demand is not paid. The tactics used in these campaigns can be convincing to a recipient unaware of these scams; however, these threats are not credible. The NJCCIC recently highlighted a widespread campaign that circulated in June.
The NJCCIC advises against paying any ransom as these scams are not considered credible threats. Additionally, we suggest that users consider searching the embedded Bitcoin address at bitcoinabuse.com/reports for reported fraud or extortion.
It is important to note that this graphic appears to show Bitcoin Blackmail threats diminishing in July, as Emotet clearly leads as the most prevalent threat; however, Bitcoin Blackmail attempts still doubled between June and July. This comparison also highlights the sheer size of the Emotet campaigns that surged in July.
The NJCCIC recommends users educate themselves and others on these continuing email-based threats and tactics to reduce victimization.