Multiple Phishing Campaigns Target O365 Credentials
NJCCIC Alert
Original Release Date: 7/17/2020
Summary
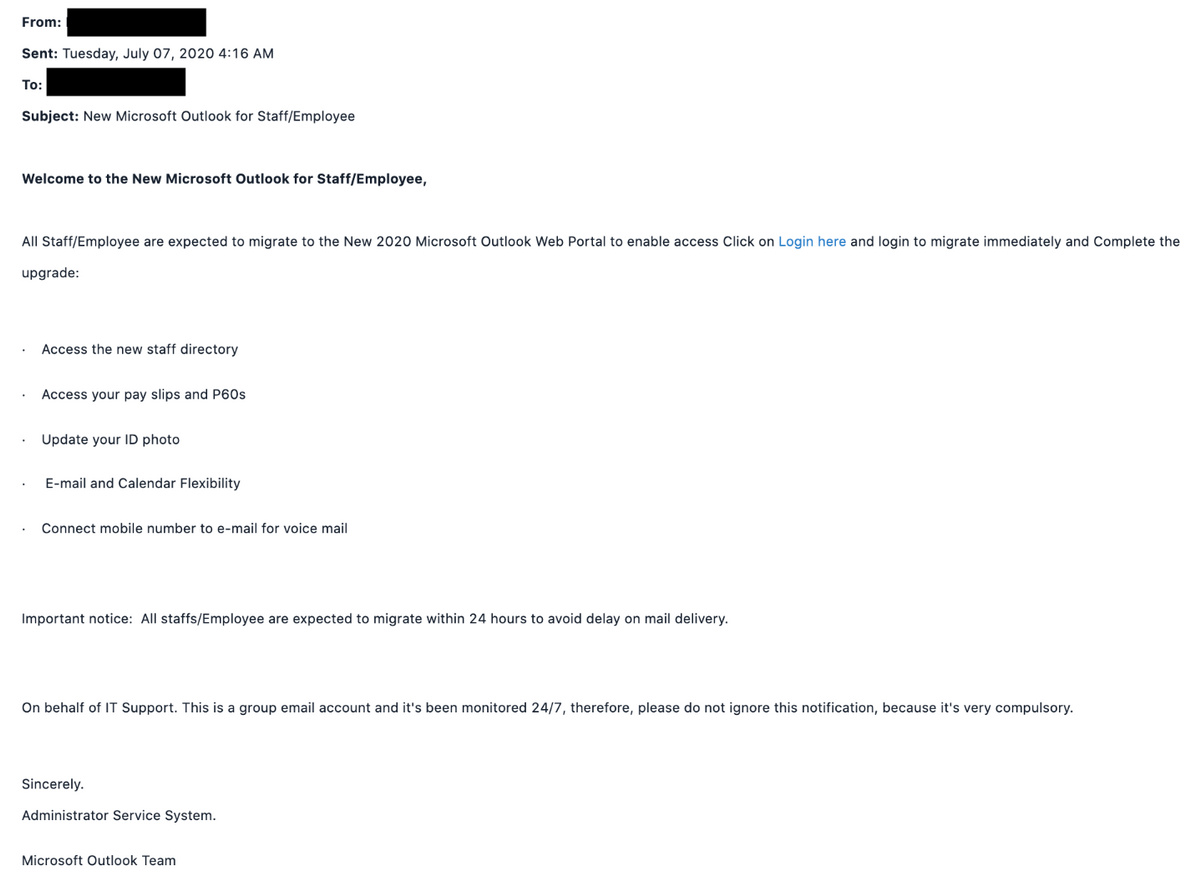
Multiple phishing campaigns have been identified targeting Microsoft Office 365 (O365) users in an attempt to steal login credentials. In one of the campaigns, the phishing email mimics an automated official notification from the Outlook team on behalf of the recipient’s organization. The email urges recipients to upgrade Outlook services within 24 hours to avoid a delay in receiving emails and contains an embedded link to the convincing spoofed login page. If the link is clicked and credentials are entered, the user’s login, and any other information stored on linked accounts using the same O365 credentials, will be compromised.
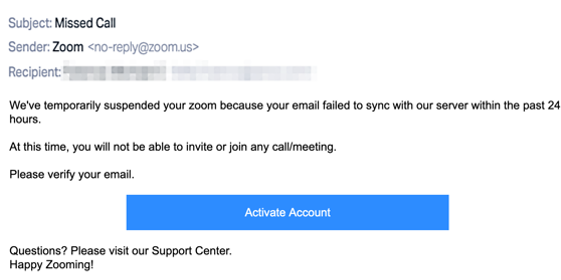
A very similar campaign has been spotted spoofing an official Zoom email address and impersonating a legitimate automated Zoom notification. The recipient is warned that their Zoom account was temporarily suspended and they will not be able to attend meetings or calls until the account is reactivated by clicking on the embedded link, which directs the user to a spoofed O365 login page. Both campaigns portray a sense of urgency and are very convincing with few, if any, grammatical errors. Compromised O365 credentials could be used in various future attacks, such as Business Email Compromise (BEC) scams.
Recommendations
The NJCCIC recommends users educate themselves and others on these continuing threats and tactics to reduce victimization. Users are advised to avoid clicking links, opening attachments, or providing personal or financial information in response to emails from unknown senders, and exercise caution with emails from trusted senders. If you are unsure of an email’s legitimacy, contact the sender via a separate means of communication. We also advise users to refrain from taking action on unsolicited emails claiming that a service will be suspended, and instead, navigate to the official site to verify information. For additional recommendations please see NJCCIC Best Practices.