Online Payment System Scams
Garden State Cyber Threat Highlight
Original Release Date: 1/7/2021
People have an expectation of security when making online payments and transactions, and want to ensure all personal information is protected and their funds are secured. They may use popular online payment systems to instantly accept and send money, such as PayPal, Venmo, Stripe, and others. Despite fraud protection and detection measures for these technological conveniences, cybercriminals take advantage of the opportunity to use social engineering tactics to target people who use these online payment systems. We provide examples and recommendations to educate users on these continuing threats and tactics in order to reduce victimization.
PayPal Phishing Emails
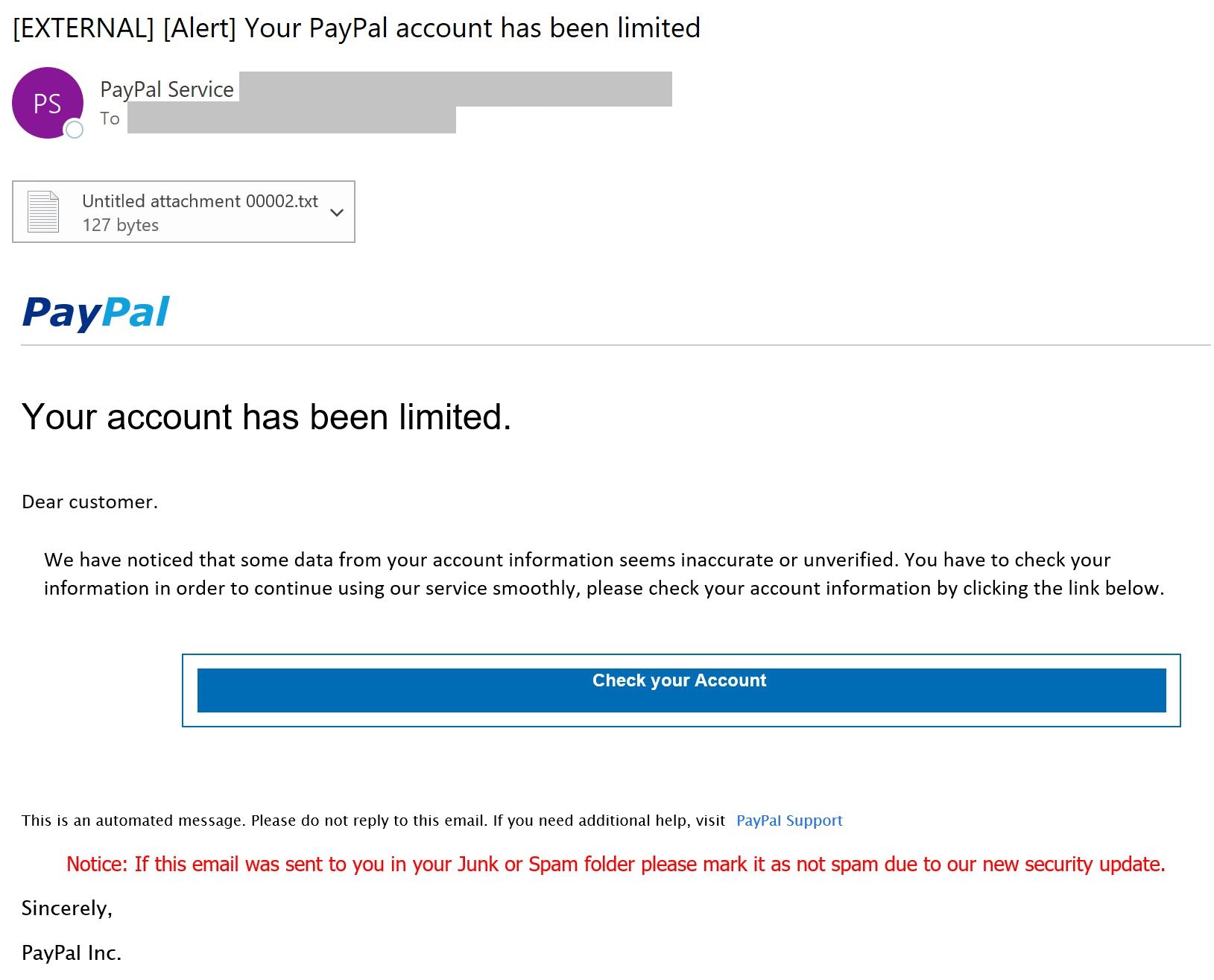
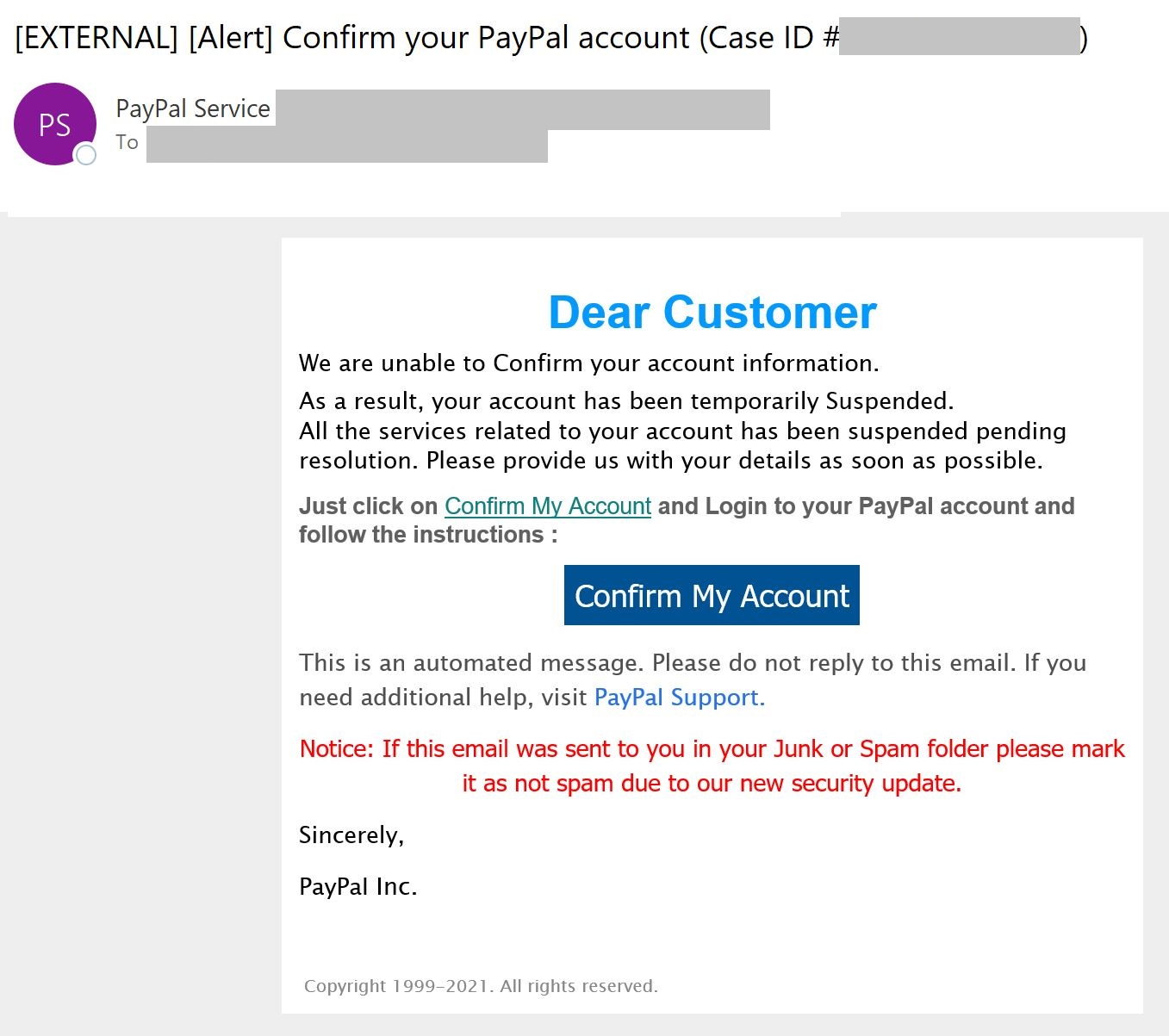
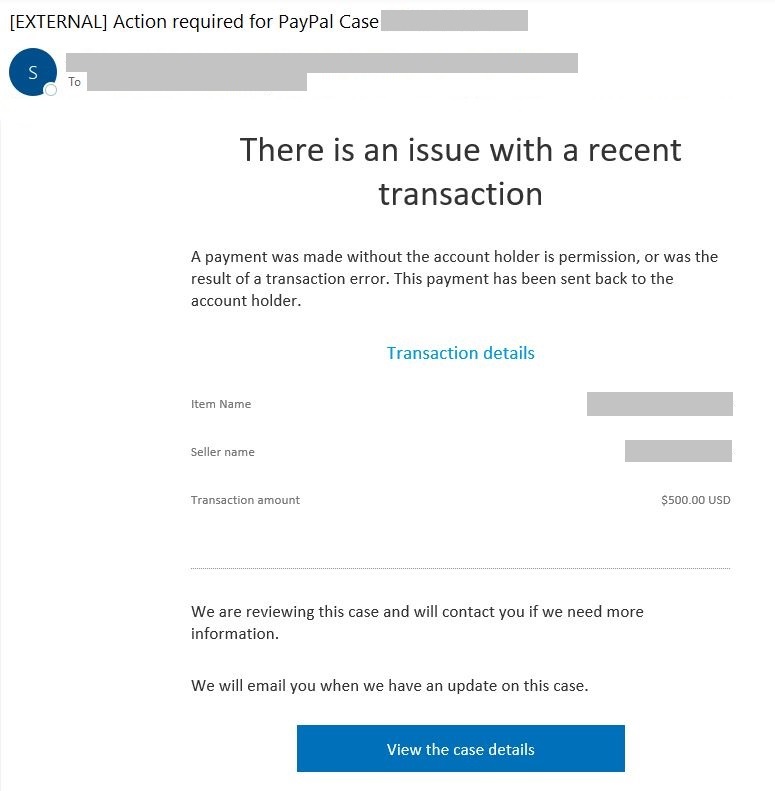
The NJCCIC observed several phishing campaigns purporting to be legitimate emails from PayPal notifying users of account and transaction issues. They contain links in colored boxes or attachments that, if clicked, directs users to a spoofed PayPal login page designed to harvest user credentials and sensitive information. These messages also convey a sense of urgency and contain grammatical errors. Emails are not personalized and, instead, are addressed to “customer.” There is also a note to mark the email as not spam due to a new security update, which creates a false sense of security.
Additional Scams
Cybercriminals have used social engineering tactics in additional online payment system scams. A PayPal SMiShing scam claimed the user’s account is limited and to click on a link to log into and verify the account. It further collects sensitive information, such as name, date of birth, address, and bank details. According to PayPal, accounts may be limited to protect users from potential losses and review any fraudulent activity, such as unauthorized use, account limits, higher-risk activity, and inactive accounts; therefore, it may difficult to discern a legitimate communication from a suspicious one.
A Venmo vishing scam involved a caller claiming to be from Venmo Support to inform them someone was trying to hack their account and the support representative was trying to stop the attempt. The caller revealed the target’s password and sent him a code to his phone to verify his identity. Once the code was received and revealed to the caller, the money was instantly withdrawn.
A Stripe phishing scam purported to be a notification that a new device has signed into their Stripe account. If the user does not recognize the device, they can click on the link to update their password. Although the email appeared legitimate and urgent, the link directed to a non-Stripe domain and the spoofed login page was not representative of Stripe’s real login page.
Recommendations
The NJCCIC recommends users practice good cyber hygiene to protect their financial information and accounts.
- Use unique, complex passwords for all accounts. Unique passwords for each account prevent password reuse attacks, in which threat actors obtain your password for one account and use it to compromise an additional account using the same credentials.
- Enable multi-factor authentication (MFA) where available. MFA is the use of two or more factors to authenticate to an account or service. This significantly reduces the risk of account compromise via credential theft in which your password has been exposed. Even if a cybercriminal obtains a user’s username and password, they will be unable to access that user’s account without their second factor. The NJCCIC encourages users to choose authentication apps, hardware tokens, or biometrics as a second factor over SMS-based authentication due to the risk of SIM-swapping, though using any form of MFA is beneficial. The website TwoFactorAuth.org maintains a comprehensive list of websites that offer MFA.
- Refrain from sharing login credentials or other sensitive information. Login credentials and other sensitive information should not be shared with anyone or saved on your computer or other platforms.
- Exercise caution with communications. Stay calm and think before reacting. Most businesses will not send communications requesting sensitive information or downloading attachments. Before providing sensitive information, confirm the legitimacy of the message or request via a separate means of communication—such as telephone—obtained directly from official websites, bills, or welcome emails.
- Navigate directly to websites. Navigate directly to authentic or official websites by typing the legitimate URL into the browser instead of clicking on links in messages, and refrain from entering login credentials on websites visited via links delivered in messages. Once logged in, check to see if there are any notifications. If not, then delete the suspicious communications.
- Use secure websites. When sharing personal or financial information, ensure you are using verified, secure, and encrypted websites.
- Update passwords immediately following a data breach or potential compromise. Use a resource, such as haveibeenpwned.com, to determine if your information, such as an account password, has been revealed in a public data breach. Change exposed passwords for every account that uses it to protect against account compromise.
- Keep devices up to date. Stay informed about publicly-disclosed vulnerabilities and update devices—including firmware—to the latest version to ensure they are patched against known vulnerabilities that could be exploited by threat actors to gain unauthorized access to your device and/or data. If a device is unable to receive updates from the vendor, consider not purchasing or discontinuing use of the device.
- Secure physical devices. Safeguard devices and ensure a password/passcode is enabled for all devices to prevent unauthorized access in the event a device is lost or stolen.
- Review accounts and report suspicious activity. Review account transactions and activity and report any suspicious activity, identity theft, and/or fraud to your financial institution, local police department, and/or the Federal Trade Commission (FTC). You may also report cyber incidents to the NJCCIC via the Cyber Incident Report form.
Resources