Ransomware: The Current Threat Landscape
Garden State Cyber Threat Highlight
Original Release Date: 2/4/2021
Ransomware is still prevalent and evolving in our current threat landscape as predictions for 2021 indicate that the number of ransomware attacks are likely to increase. The NJCCIC continues to receive reports of ransomware incidents impacting NJ businesses, organizations, and private citizens, resulting in operational disruptions, financial loss, and/or data exfiltration. Threat actors gain access to networks typically through internet-facing vulnerabilities and misconfigurations, remote desktop protocol (RDP) connections, third parties and managed service providers (MSPs), and phishing emails. They also use one or more extortion tactics, including denying access to encrypted files, stealing data, threatening a data breach, and/or distributed denial-of service (DDOS) attacks. We explore the current threat landscape of the new year and provide recommendations to educate users and organizations and increase resiliency to ransomware attacks.
Despite the average ransom payment decreasing at the end of last year, it was still a great year for threat actors who profited over $350 million from ransom payments in 2020, as top earning groups included Ryuk, Snatch, and Sodinokibi. Threat actors primarily targeted healthcare, education, critical infrastructure, and government sectors. These sectors continue to be a primary target in 2021, especially with the ongoing pandemic. Industrial organizations that require high uptime are also a prime target as they may be more inclined to pay the ransom to avoid disruptions to operations that could impede services and result in great financial loss. When critical systems and devices are in constant use, they are not readily available for security updates and are vulnerable to exploitation.
After ringing in the new year, new ransomware variants emerged. Babuk Locker employs new tactics of multi-threading encryption and Windows Restart Manager exploitation, and shares common traits with the successful Ryuk and Sodinokibi variants. Vovalex is distributed through pirated software impersonating the popular CCleaner Windows utility and may be the first ransomware written in “D” language to bypass detection.
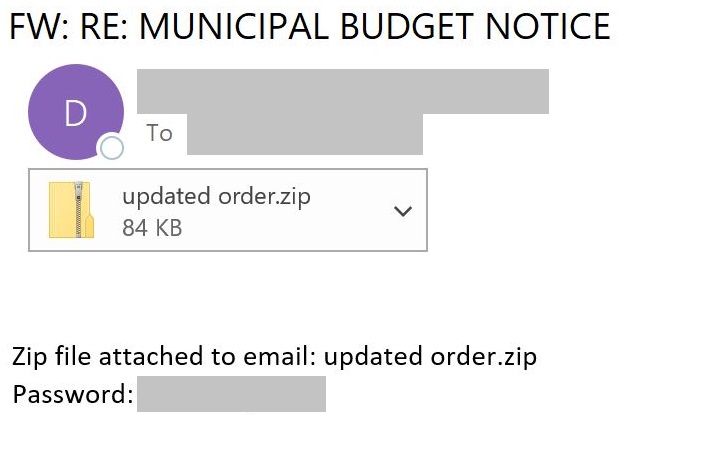
Ransomware attacks are generally secondary to initial malware infections, such as Emotet and TrickBot. The NJCCIC observed multiple blocked phishing campaigns in attempts to deliver Emotet to NJ state employees in January 2021. In these campaigns, emails contained either Microsoft Word attachments, password-protected ZIP files with Word documents, or URLs linking to the download of Word documents. These Word documents contained macros that, if enabled, download and install Emotet. Subject lines contained luring themes of invoices, shipping notices, COVID-19, or other themes creating a sense of urgency. Some emails also appeared to look like responses to previous conversation threads and contained a password for the ZIP file, as displayed in the phishing email example. In the earlier part of the purported conversation, the email claims that access to information was temporarily removed and, therefore, the workaround was to attach a password-protected ZIP file.
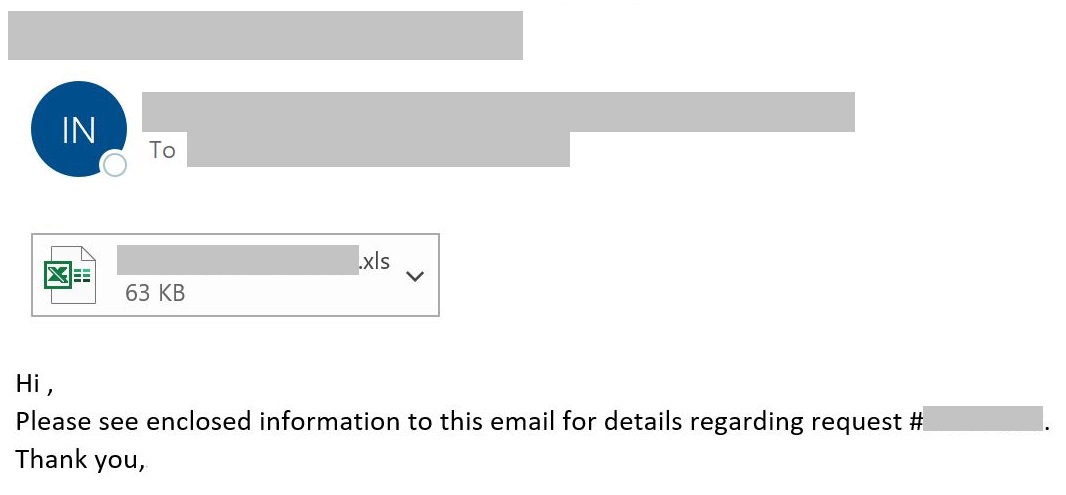
After Emotet was disrupted by a global law enforcement operation, TrickBot is still an imminent threat attempting to take Emotet’s place. The NJCCIC observed blocked TrickBot campaigns with similar lures to Emotet campaigns and containing Microsoft Excel attachments and subject lines pertaining to specific sales reports in the phishing example. Additionally, a new TrickBot module, dubbed Masrv, uses the Masscan open-source utility to perform local network reconnaissance for other systems with open ports in order to deploy other modules and move laterally to infect new systems.
Ransomware can also infect and spread as a result of previously unresolved network compromises. When attacks happen, the priority is to recover data, restore systems, and ensure business is operating again. It is recommended to also identify the root cause and secure the network. Unfortunately, organizations may fail to review the lessons learned from the incident, only to find themselves victimized by the same ransomware variant using the same attack vector and end up paying the ransom a second time. This is another reason not to pay the ransom. The threat actors already had access to the network, remained undetected for a period of time, and can easily target and attack again. File restoration and deletion of stolen data are also not guaranteed upon payment of the ransom, and paying the ransom further enables the lucrative business of ransomware attacks to continue.
Recommendations
Organizations can employ the following defensive measures to create a more cyber resilient environment to reduce the risk of ransomware attacks:
- Security awareness training. Train employees to help better understand cyber threats and provide a strong line of defense.
- Exercise caution with communications. Refrain from divulging sensitive information via phone, text messaging, or email without verifying the requestor via a separate means of communication before taking any action.
- Refrain from sharing or saving login credentials or other sensitive information. Login credentials and other sensitive information should not be shared with anyone. Avoid auto-saving passwords, payment card numbers, or contact information when prompted by your operating system, browser, website, or applications.
- Navigate directly to websites. Navigate directly to authentic or official websites by typing the legitimate URL into the browser instead of clicking on links in messages, and refrain from entering login credentials on websites visited via links delivered in messages.
- Use secure websites. When sharing personal or financial information, ensure you are using verified, secure, and encrypted websites.
- Use unique, complex passwords for all devices/accounts. Unique passwords for each device/account prevents password reuse attacks, in which threat actors obtain your password for one account and use it to compromise an additional account using the same credentials.
- Change the default password. Default passwords for devices/accounts can be used to gain unauthorized access.
- Secure physical devices. Safeguard devices and ensure a password/passcode is enabled for all devices to prevent unauthorized access.
- Keep devices up to date. Stay informed about publicly-disclosed vulnerabilities and update devices—including firmware—to the latest version to ensure they are patched against known vulnerabilities that could be exploited by threat actors to gain unauthorized access to your device and/or data. If a device is unable to receive updates from the vendor, consider not purchasing or discontinuing use of the device.
- Implement protective technologies. IT departments are advised to implement endpoint detection and response software, host-based firewalls, device and file encryption, and keep devices updated with latest security patches. The encryption of sensitive data at rest and in transit is highly encouraged to reduce the likelihood of threat actors publicly exposing any stolen data.
- Adopt a third-party management program. Implement security protections and controls to safeguard client networks and data as well as limit the impact if an incident occurs. Ensure any contracts and agreements with third-party vendors detail the necessary cybersecurity requirements.
- Defense-in-depth cybersecurity strategy. Implement a defense-in-depth cybersecurity strategy and access controls, including applying the Principle of Least Privilege, enabling multi-factor authentication (MFA), utilizing a Network Access Control (NAC) solution for connectivity into internal networks, and establishing a comprehensive data backup plan.
- Network and resource segmentation. Distribute servers and critical data in different data centers to ensure they are located on different networks with diverse paths.
- Firewall and router configurations. Configure firewalls and routers primarily to block unauthorized IP addresses, close unnecessary ports, disable port forwarding, and prevent DNS and ping-based volumetric attacks.
- Network traffic monitoring. Understand your own network traffic patterns, continuously monitor network traffic, and recognize abnormal activity.
- Vulnerability assessment and penetration testing. Regularly check for and remediate exploitable security flaws and vulnerabilities.
- Backup devices. Protect your information from malware, hardware failure, damage, loss, or theft by keeping multiple, tested copies offline with at least one in a separate and secure location.
- Establish a resiliency plan. Establish Business Continuity, Disaster Recovery, and Incident Response Plans to maintain continuity in the event of a ransomware attack.
- Remediate compromised devices. It is important to monitor logs for signs of access and exfiltration. When practical, wipe and reimage hard drives.
- Incident reporting. Report malicious cyber activity to the NJCCIC via the Cyber Incident Report form and/or report data breaches to the NJCCIC via the Data Breach Report form.
References
- NJCCIC Ransomware: Risk Mitigation Strategies
- NJCCIC Ransomware Threat Profiles
- NJCCIC Mitigating the Risk of Malware Infections
- NJCCIC Cybersecurity 101: Best Practices
- NJCCIC Don’t Take the Bait! Phishing and Other Social Engineering Attacks
- NJCCIC Supply Chain: Compromise of Third-Parties Poses Increasing Risk
- CISA Ransomware Guidance and Resources
- CISA & MS-ISAC Ransomware Guide
- CIS Security Primer Ransomware
- CIS Security Primer General Security Recommendations
- CIS Want to Keep Your Data? Back It Up!
- US-CERT Data Backup Options