Recent Phishing Campaigns Target NJ State Employees in Attempts to Deliver Ursnif Trojan
NJCCIC Alert
Original Release Date: 7/10/2020
Summary
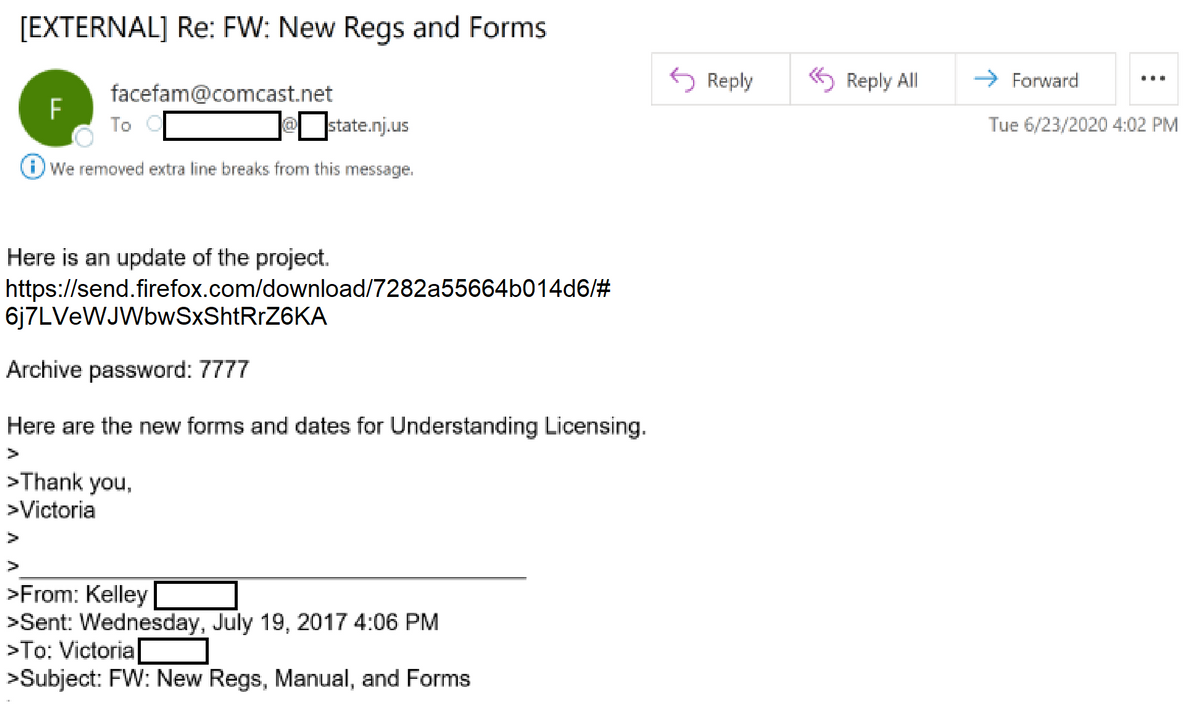
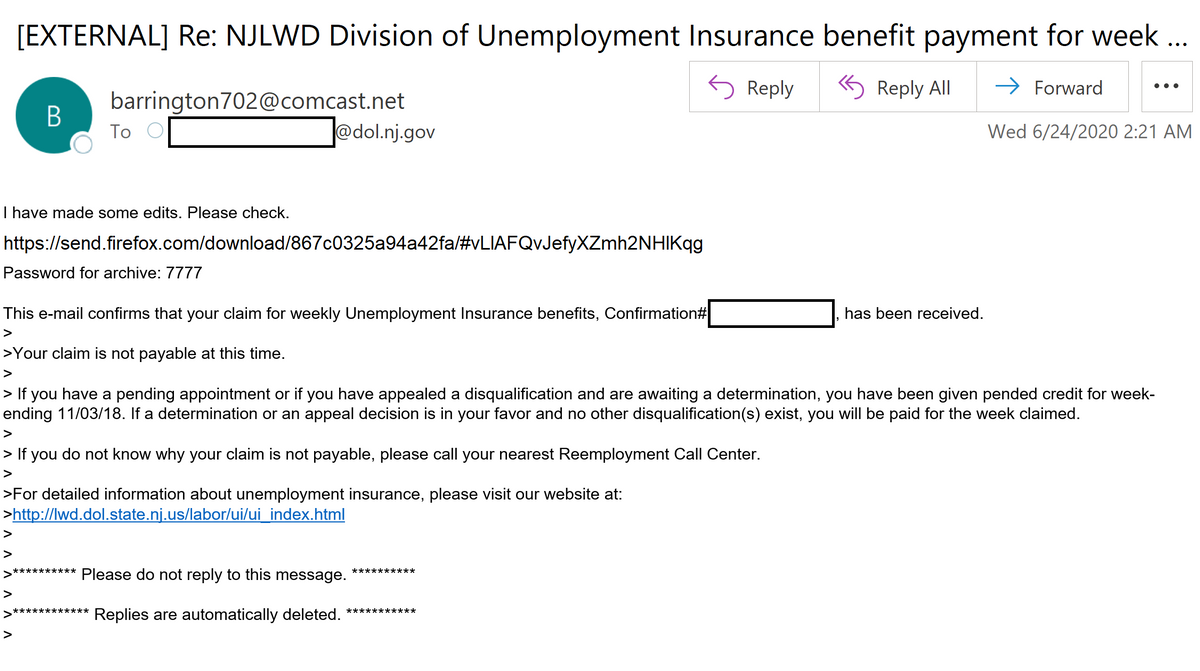
The NJCCIC observed phishing campaigns intending to deliver the Ursnif banking trojan, which is used to steal banking credentials and other sensitive information. The blocked emails attempt to convince recipients to click on a link that will initiate the download of a password-protected ZIP archive, which contains a VBScript file that, if executed, downloads the Ursnif trojan. Password-protected ZIP archives are commonly used by threat actors to deliver malicious files. Email security tools are often unable to properly scan files contained within ZIP archives and are therefore more likely to be delivered to an end user’s inbox. One method to help identify potentially malicious emails using password-protected ZIP archives is to block or quarantine emails when they also contain the password within the same email. In a legitimate scenario, the password would be sent in a separate email; otherwise, password protecting the file is futile.
In this example, the message appears to be part of an existing email thread, references a project and licensing, and uses a subject line that references registration in attempts to emit a sense of legitimacy and interest to the recipient. The aforementioned red flag of providing the archive password within the email is also present.
In this example, the recipient email address is associated within the NJ Department of Labor and the email references the NJ Department of Unemployment Insurance in the subject line. This email, like the previous one, contains a URL that links to a ZIP archive, with the password provided in the email. At the bottom of the email, there is a link that appears to lead to the NJ unemployment insurance website. This link directs the user to a nj.gov “Page Not Found;” however, it does redirect to the legitimate Division of Unemployment Insurance myunemployment.nj.gov website.
Recommendations
The NJCCIC recommends avoiding clicking on links delivered in emails from unknown senders and exercising caution with those received from known senders. Additionally, refrain from opening files that come within password-protected ZIP archives when the password is delivered in the same email. To determine the legitimacy of a suspicious email, contact the sender via a separate means of communication. Users are encouraged to educate themselves and others on current cyber threat tactics and techniques in order to reduce victimization.