The Cybersecurity of Critical Infrastructure
Garden State Cyber Threat Highlight
Original Release Date: 2/18/2021
The cybersecurity of critical infrastructure and key resources have increasingly become a concern as cyberattacks affect the confidentiality, integrity, availability, and privacy of information and information systems. Cybercriminals attempt to exploit and degrade these systems in order to disrupt operations and potentially impact public health and safety. Recent events highlight the risk to critical infrastructure and reinforce the need for resiliency plans to ensure risk management, business continuity, disaster recovery, and incident response.
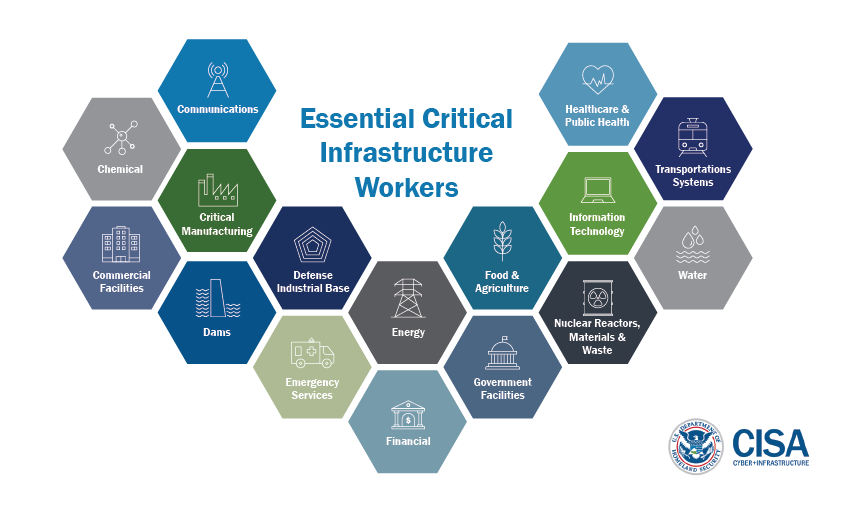
What is Critical Infrastructure?
Critical infrastructure includes the physical and networked systems and assets that are so vital that their incapacity or destruction would have a debilitating impact on physical security, cybersecurity, economic security, public health and safety, or any combination thereof. There are 16 essential critical infrastructure sectors, which include a vast network of communications, services, utilities, and facilities necessary to maintain normalcy in daily life. Transportation, commerce, clean water, and electricity are some examples of vital systems that are susceptible to cyberattacks. In addition, some systems are interconnected or dependent on another; therefore, the disruption of or attack on one system may affect the operation of another system and potentially have a cascading effect.
Critical Infrastructure Attacks
Critical infrastructure are attractive targets for threat actors. Domestic cyber incidents, such as the 2013 compromise of the Bowman Avenue Dam in Rye Brook, NY, the 2018 ransomware attack at a North Carolina water utility, and the 2020 compromise of critical infrastructure in the SolarWinds Orion supply chain, demonstrate how threat actors can target and infiltrate vulnerable systems, gain access, and escalate privileges. Most recently, the compromise of a Florida water treatment plant involved the exploitation of a popular remote desktop application to infiltrate systems and modify the levels of a chemical used in the water treatment process. An attentive operator noticed the unauthorized access and corrected the levels before any harm came to the servicing population. Other details revealed that the plant’s operational technology (OT) network was externally accessible, computer networks were running operating systems with end of life status and lack of security updates, and systems shared the same password for remote access without multi-factor authentication. Vulnerabilities in critical infrastructure can lead to compromise and potentially affect public health and safety. The mitigations and prevention of public harm reinforces how security controls, including security awareness training, are critical in keeping systems secure. Technology and processes are important components of security; however, skilled, trained, and alert staff are a vital investment.
Cybersecurity Concerns of Critical Infrastructure
Although the recent Florida water treatment plant attack was detected and mitigated before reaching a greater level of danger, it highlights the public risks and exposure, and the need to strengthen the cybersecurity of critical infrastructure. Many critical infrastructure systems may be outdated, unpatched, and exposed to the Internet, leaving them vulnerable to compromise. The increasing instances of security breaches and cyberattacks is a growing concern and could reveal credentials for access to systems; therefore, they should be taken seriously as they could attract more successful attacks against critical infrastructure. After being considered an afterthought for many years, cybersecurity spending for critical infrastructure is expected to increase by $9 billion over the next year as efforts are focused on ensuring operational technology is safeguarded, while also allowing operations to be securely monitored and managed remotely by authorized personnel. Cybersecurity concerns are driving organizations to regularly assess cyber threats, identify individual vulnerabilities, and adopt security measures to increase cyber defenses and provide protective safeguards from cyberattacks that could quickly inflict real-world physical harm.
Recommendations
The NJCCIC recommends users and critical infrastructure owners and operators apply cybersecurity best practices to reduce the risk and potential impacts of a cyberattack.
- Implement protective technologies. IT departments are advised to implement endpoint detection and response software, host-based firewalls, device and file encryption, and keep devices updated with latest security patches. The encryption of sensitive data at rest and in transit is highly encouraged to reduce the likelihood of threat actors publicly exposing any stolen data.
- Adopt a third-party management program. Implement security protections and controls to safeguard client networks and data as well as limit the impact if an incident occurs. Ensure any contracts and agreements with third-party vendors detail the necessary cybersecurity requirements.
- Defense-in-depth cybersecurity strategy: Implement a defense-in-depth cybersecurity strategy and access controls, including applying the Principle of Least Privilege, enabling multi-factor authentication (MFA), utilizing a Network Access Control (NAC) solution for connectivity into internal networks, and establishing a comprehensive data backup plan.
- Network and resource segmentation: Distribute servers and critical data in different data centers to ensure they are located on different networks with diverse paths. For critical infrastructure, segment information technology (IT) and operational technology (OT) networks.
- Firewall and router configurations: Configure firewalls and routers primarily to block unauthorized IP addresses, close unnecessary ports, disable port forwarding, and prevent DNS and ping-based volumetric attacks.
- Network traffic monitoring: Understand your own network traffic patterns, continuously monitor network traffic, and recognize abnormal activity.
- Remediate compromised and/or stolen devices. It is important to monitor logs for signs of access and exfiltration. When practical, wipe and reimage hard drives. Also, utilize remote administration and data wiping solutions to regain control of devices if they cannot be physically accessed.
- Keep devices up to date. Stay informed about publicly-disclosed vulnerabilities and update devices—including firmware—to the latest version to ensure they are patched against known vulnerabilities that could be exploited by threat actors to gain unauthorized access to your device and/or data. If a device is unable to receive updates from the vendor, consider not purchasing or discontinuing use of the device.
- Vulnerability assessment and penetration testing: Regularly check for and remediate exploitable security flaws and vulnerabilities. Identify any vulnerabilities, interdependencies, capabilities, and cascading effects of impacts to critical infrastructure.
- Backup devices. Protect your information from malware, hardware failure, damage, loss, or theft by keeping multiple, tested copies offline with at least one in a separate and secure location.
- Establish a resiliency plan: Establish Business Continuity, Disaster Recovery, and Incident Response Plans to maintain continuity in the event of an attack.
- Implement strategies for emergency situations. It is important to implement strategies for emergency situations, including when human life is at risk. The strategy may include planning and tabletop exercises, preparation and training, and monitoring.
- Invest in security awareness training. Invest the time, money, and resources so users understand risks, the latest cyber threats, and best practices.
- Use unique, complex passwords for all accounts. Unique passwords for each account prevent password reuse attacks, in which threat actors obtain your password for one account and use it to compromise an additional account using the same credentials.
- Refrain from sharing login credentials or other sensitive information. Login credentials and other sensitive information should not be shared with anyone, posted in plain view, or saved on your computer or other platforms.
- Exercise caution with communications. Refrain from divulging sensitive information via phone, text messaging, or email without verifying the requestor via a separate means of communication before taking any action.
- Navigate directly to websites. Navigate directly to authentic or official websites by typing the legitimate URL into the browser instead of clicking on links in messages, and refrain from entering login credentials on websites visited via links delivered in messages.
- Use secure websites. When sharing personal or financial information, ensure you are using verified, secure, and encrypted websites.
- Change the default password. Default passwords for accounts/devices can be used to gain unauthorized access.
- Update passwords immediately following a data breach or potential compromise. Use a resource, such as haveibeenpwned.com, to determine if your information, such as an account password, has been revealed in a public data breach. Change exposed passwords for every account that uses it to protect against account compromise.
- Check privacy and security settings. Checking these settings will help manage your cyber risk and limit how and with whom you share information.
- Lock screens. When stepping away from your computer or device, the manual lock function helps to protect the information stored on or accessible from your computer. Also, check security settings or policies to automatically lock screens after inactivity.
- Secure physical devices. Safeguard devices and ensure a password/passcode or an additional authentication factor is enabled for all devices to prevent unauthorized access in the event a device is lost or stolen, or USB or external device is inserted.
- Report incidents: Report malicious cyber activity to the NJCCIC via the Cyber Incident Report form.
Resources
- NJCCIC Cybersecurity Best Practices
- NJCCIC Stop What You Are Doing and Enable MFA
- NJCCIC Don’t Take the Bait! Phishing and Other Social Engineering Attacks
- NJCCIC Ransomware: Risk Mitigation Strategies
- CISA Critical Infrastructure Vulnerability Assessments
- CISA Industrial Control Systems
- CISA Seven Steps to Effectively Defend Industrial Control Systems
- CISA Recommended Cybersecurity Practices for Industrial Control Systems
- NIST Framework for Improving Critical Infrastructure Cybersecurity
- NIST Responsible Use of Positioning, Navigation, and Timing Services