'Tis the Season for Holiday Phishing
Garden State Cyber Threat Highlight
Original Release Date: 12/3/2020
‘Tis the Season for Holiday Phishing
Image Source: Security Weekly
The holiday season is here and the NJCCIC has observed several holiday related phishing campaigns attempting to deliver emails to New Jersey state employees with the intent to install malware or steal users' credentials. Due to the global pandemic, users will likely shop online from home and virtually gather with family and friends. They may receive phishing emails impersonating known retailers, businesses, shipping companies, and financial institutions that also convey a sense of urgency. Users may also receive phishing emails from popular video conferencing platforms, such as Zoom, to convince them to take action to reschedule a meeting or activate/reactivate their account. Phishing emails often contain links or attachments that, if clicked or opened, install malware or direct users to spoofed websites to steal users’ credentials or information for financial theft and fraud. We provide examples of these phishing emails below to educate users on these continuing threats and tactics in order to reduce victimization.
The NJCCIC recommends users exercise caution with links and attachments received from unknown contacts or file-sharing platforms, check the sender’s information for legitimate domains, confirm the email’s legitimacy via a separate means of communication, navigate directly to authentic vendor websites, keep applications up to date, enable multi-factor authentication where available, and implement a defense-in-depth cybersecurity strategy. We also recommend reviewing the NJCCIC product Don’t Take the Bait! Phishing and Other Social Engineering Attacks and the NJCCIC’s Cybersecurity Best Practices webpage for more information on how to keep accounts and data safe.
Shopping Sales and Coupons
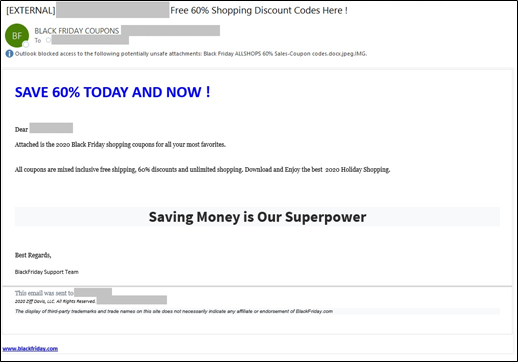
Phishing campaigns may entice users with special offers and convey a sense of urgency with designated shopping days, such as Black Friday. This message may contain various “shopping discount codes” in the subject line. Attachments may end in .scr or .img that, if clicked and executed, install the QuasarRAT trojan.
Shipping and Delivery Notifications
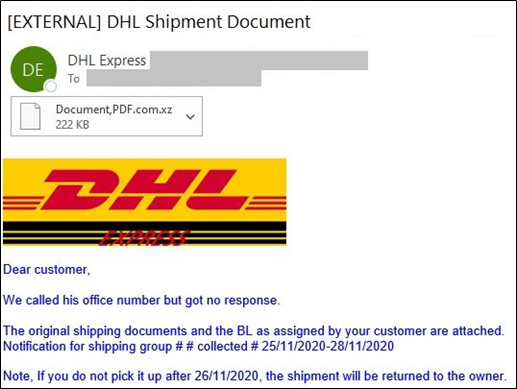
There has been a dramatic increase in the number of phishing emails impersonating shipping companies—such as DHL, Amazon, and FedEx. Cybercriminals target users with shipping and delivery notifications and report delivery issues or tracking details to convince them to disclose personal information. This message may contain the subject line “DHL Shipment Document” and attachments that, if clicked and executed, install the Agent Tesla trojan.
Financial Account Information
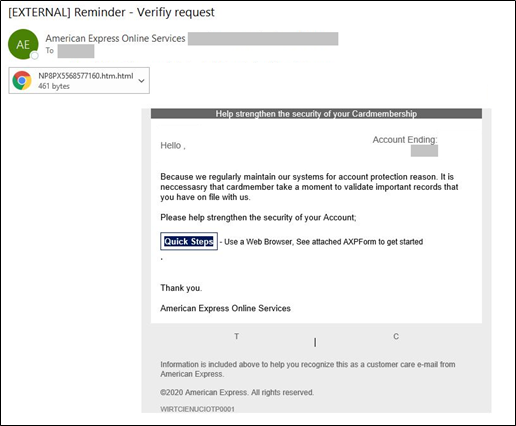
Cybercriminals may attempt to target users to update financial account information. In this example, the phishing email contains spelling errors and may contain keywords—such as reminder, alert, or important update—in the subject line. It also contains an HTML attachment or phishing URL to review their account that, if opened, directs them to a spoofed American Express authentication page designed to harvest email credentials and banking accounts. Other examples include subject lines of "daily transaction notice," "usage is restricted," and "your account is locked."