Spotting a Spoofing
Informational Report
Original Release Date: 11/19/2020
Now more than ever, it is becoming increasingly important to take caution before clicking - particularly as it pertains to email. Cybercriminals are persistently evolving their tactics for attack, finding new ways to successfully exploit an unsuspecting user. One of the most common attack vectors is malicious emails. While you may think you are receiving an email from a known contact or trusted organization, this email could be from a cybercriminal attempting to convince you to click on a link or open an attachment that facilitates credential and data theft or the delivery of malware. Stolen credentials can provide threat actors with the opportunity to steal data, financial information, funds, and conduct subsequent attacks, while malware can facilitate data theft and the installation of additional malware, such as ransomware. Spoofing is a tactic often employed by threat actors in these malicious email attempts; however, understanding how to identify spoofing techniques can prevent victimization.
What is Email Spoofing?
Email spoofing occurs when someone pretends to be a trusted source by manipulating the email sender information. They can change the sender display name and/or email address to that of a known or trusted entity, such as an employer, a close friend or family member, a recognizable organization, or public figure. Cybercriminals depend on the trust between you and this source to convince you to take action on the email, such as clicking a link, opening an attachment, or divulging sensitive information. For example, when a letter is sent via postal mail, the address of the recipient needs to be correct and legitimate; otherwise, the letter will not arrive at the intended destination. The sender, however, can write any address in as the return address (sender address). This is how we can think of email, the sender information displayed as part of the user interface can be spoofed and should not be trusted. Two methods of spoofing used by threat actors are display name spoofing and email address spoofing.
Display Name Spoofing and Email Address Spoofing: What's the Difference?
While both these attacks fall under spoofing, there are key differences that set them apart. Display name spoofing takes place when a threat actor changes the display name visible in the sender line of an email to that of a known source, which causes the recipient to trust the email. Threat actors rely on this tactic as it is trivial to execute and recipients often only take the time to verify the display name – not the corresponding email address – when choosing to act on an email. In addition, many email applications on mobile devices only show the display name by default; a user would have to take extra steps to view and verify the corresponding email address. Email address spoofing, on the other hand, takes place when the threat actor changes the sender’s email address displayed to the user. This is often done along with display name spoofing, making the sender information visible to the recipient appear legitimate. While email address spoofing is more involved than display name spoofing, neither is difficult to execute. Both techniques can be conducted with ease and significantly increase the likelihood that the threat actor will succeed using this email attack vector.
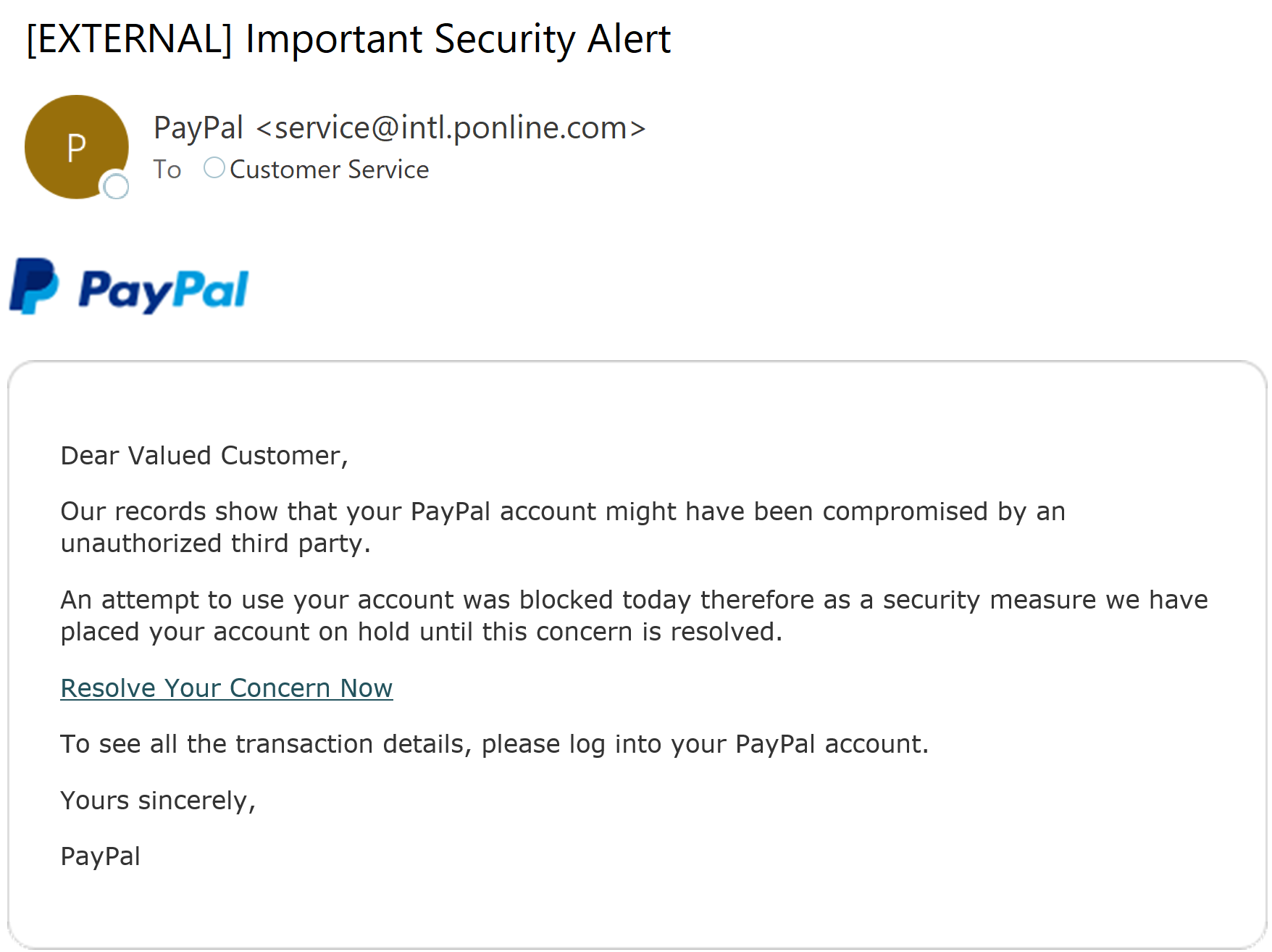
Image: Example PayPal Display Name Spoofing
How can you identify email spoofing?
Check the Sender
Display name spoofing is relatively easy to identify. If you are on your phone’s email app, you may have to expand the email’s "To" information in order to see the full email address of the sender. In simple display name spoofing attempts, the display name will appear legitimate, but the associated email address will not correlate with whom the sender claims to be. Be sure to inspect the sender information slowly for indications of display name and/or email address spoofing. Cybercriminals may also use email domain names that resemble that of legitimate domain names in order to trick the email recipient. For example, a threat actor could use the email address info@googIe[.]com and claim the email is from Google; however, what looks like the lowercase “L” in Google was replaced with an uppercase “I,” only giving the appearance of legitimacy.
Check the Email Header
The information sent with an email includes much more than what we see in our user interface. There is additional data that can be found within the email header, which is a bulk of information about the email – such as timestamps, the recipient and sender, reply-to addresses, and the servers used to transfer the message. Email headers are not typically seen in plain sight, and there are different methods to access email headers depending on the email client used.
There are certain checks to keep in mind when analyzing the email header information for anomalies or red flags. Pay attention to the ‘From’ email address, the ‘Reply-To’ address, and ‘Return-Path.' First, check that the display name is associated with the ‘From’ email address and verify the display name for minor letter changes, as they are hard to notice at first glance. Additionally, make note of the source and if it matches the Reply-To header. If a sender is spoofing the email address in the sender line of the email, the Reply-To address will be a different email address linked to an account controlled by the threat actor. Lastly, check the ‘Return-Path’ to determine where the message originated.
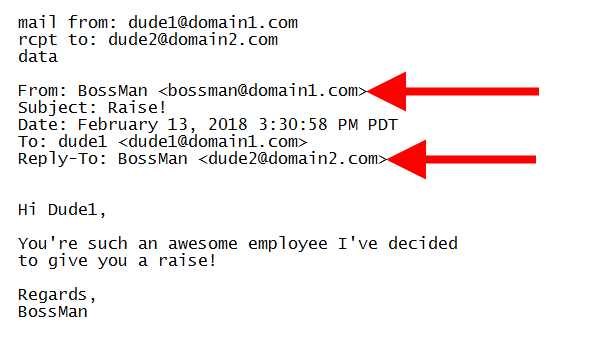
Image Source: Proofpoint
In the example above, we can see that the threat actor spoofed the email address and the display name; however, the ‘Reply-To’ address indicates that the sender is not who they purport to be. Unfortunately, engaging email spoofing is trivial; there are various resources available online to assist threat actors in their efforts. Many online tools allow users to send fake emails to anyone while pretending to be someone else, offering the ability to send a message as any email address, with some tools including features for attachments, encryption, and more.
Question the Contents
While humans are often the weakest link, they can also be an incredible asset in cyber defense and resiliency. Think critically when you sort through your emails and ask yourself if you are expecting the email. If any red flags pop up, inspect all emails with scrutiny. Urgency is a common tactic used in malicious emails; if the language used intends to push the recipient to act quickly, take a moment to ask yourself if the message makes sense. Oftentimes, we get used to the cycle of receiving and responding to emails and let our guard down, believing that everyone is who they say they are. While it may be tedious to double check emails for legitimacy, a malware infection or credential compromise resulting from a successful phishing attack using display name or email address spoofing could have lasting implications and devastating impacts. Maintaining awareness of the tactics used by cybercriminals in their exploitation efforts can help to reduce victimization and keep accounts and networks better secured.