Configuring & Securing a Home Wi-Fi Router
Technical Guide
Original Release Date: 4/5/2018
A great way to reduce your cyber risk is to ensure your home Wi-Fi network is properly configured and secured. Think about how many devices are connected to your home’s wireless network right now. In modern households, there could easily be a dozen or more connected devices. Laptop computers, tablets, video game consoles, home security cameras, smart thermostats, and smart home lighting kits all need internet access to work properly. To protect yourself and your home network from cyber threats, there are a few steps you’ll need to take. Use the instructions below to help you set up a new wireless router (home Wi-Fi network) or to audit and secure your existing set-up.
PHYSICAL SETUP
When setting up your router, there are a few things to keep in mind. Depending on what brand of router you choose, internal components may differ, but the interface and external ports that you will see are generally the same. Also, many people opt to use one device that operates as both a router and a modem. If you use a combination modem/router unit, skip the second step in the physical setup process.
-
Plug the provided coaxial cable or DSL phone line into your modem.
-
Connect the Ethernet cable from your modem into your wireless router.
-
Plug in the AC power adapters for each and then turn on the devices.
-
Connect your computer to the router either via an Ethernet cable or to the now-available Wi-Fi signal using the default password provided by the router manufacturer or the password provided to you by your internet service provider (ISP) if you acquired the router from them.
SETUP WI-FI USING THE WEB INTERFACE
Once your computer is connected to the router, you’ll need to navigate to the router's web interface. The web interface allows you to view and control what’s connected to your home's wireless network.
-
Locate the router’s web interface by entering its IP address, or “default gateway,” into the URL field of your web browser. To find the correct IP address, either consult the router’s documentation or use the following instructions on How-To Geek to locate it on your system.
-
Once located, open your web browser and type that IP address into the URL field. The address will consist of numbers separated by three periods, such as 192.168.1.1.
-
Use the setup wizard to customize your network settings. This will consist of naming your wireless network and establishing a network password. Additional recommended settings are described below.
-
Connect your devices to the Wi-Fi network using the new password.
-
You should now be online!
THE FOLLOWING ARE ALL RECOMMENDATIONS THAT CAN PROTECT YOUR NETWORK, DATA, AND IOT DEVICES:
Change the router default username and password
One of the first steps you should take to secure your Wi-Fi network is to change the default administrator username and password that comes with your router model by default. In most cases, the default username and password are publicly available online and, therefore, can be abused by threat actors to gain access to your network.
Change the network name (SSID)
Wi-Fi network names, or service set identifiers (SSIDs), can range from the mundane ("Café Hotspot") to the intimidating ("FBI Surveillance Van"). Whatever the inspiration behind your SSID is, it actually serves a more important role than just personalization. The router will likely come with a default SSID that includes information on the router’s make and model. This information can be very useful to those looking to exploit vulnerabilities contained in these routers in order to gain unauthorized access to networks. Therefore, it’s a good idea to change the SSID and to disable SSID broadcast so that the network is hidden, which requires users to manually enter the network name before connecting to it.

Enable WPA2 with AES (or WPA3, if available)
It is important to ensure that all of your personal data is properly encrypted when using devices on your Wi-Fi network. To do this, there are multiple possible wireless security protocols: Wired Equivalent Privacy (WEP), Wi-Fi Protected Access (WPA), Wi-Fi Protected Access Version 2 (WPA2), and Wi-Fi Protected Access 3 (WPA3). WEP and WPA both contain security vulnerabilities and should be avoided. WPA2 is still widely used and is a secure option as it continually changes to meet security standards and maintain interoperability. Devices that support WPA3 will continue to work with WPA2 devices for the foreseeable future. According to the Wi-Fi Alliance, WPA3 has new features for security and greater protections against password guessing attempts.
Most routers actually give you multiple options. If WPA3 is not an option, the best security mode to select is WPA2-PSK with AES encryption (sometimes labeled as WPA2-Personal). PSK stands for pre-shared key and is generally the encryption passphrase. AES a highly secure encryption standard that is officially endorsed by the National Institute of Standards and Technology (NIST) and the U.S. Government even uses it to encrypt sensitive information.
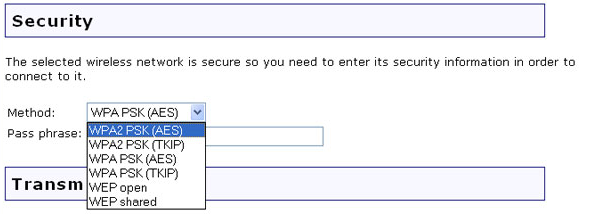
To access your router settings and change settings like the SSID and wireless security protocols do the following:
-
Use the same IP address used to change the default username and password to access the router settings.
-
Enter the router's admin username and password.
-
Change the SSID and, if you choose, disable the SSID broadcast through the provided options.
-
Select your Wi-Fi encryption, WPA3, if available, or WPA2-PSK (AES).
-
Once you select WPA2-PSK (AES), you will be prompted to enter a password. This will be your new Wi-Fi password and will be required when connecting devices to your network. An ideal password is long, complex, and hard to guess.
*Some wireless providers have their customers change Wi-Fi settings through their account website.*
Update the firmware on your router
Unlike most operating systems on computers that perform automatic updates or prompt you to install updates, the operating system of a router – known as firmware – needs to be downloaded and installed manually by the user. While this may seem tedious, often times, the provider's website has an updated version available for installation. Keeping your firmware up to date can provide a range of benefits. Firmware updates may patch vulnerabilities or correct bugs that are compromising the security of the information traversing your network. They may also upgrade encryption modules that have become outdated, adding another level of security to your devices and data.

Create separate networks to group devices
Create separate networks for devices in your home with a similar purpose and/or sensitivity. For instance, you may want to keep lights, thermostats, and surveillance cameras separate from devices like cellphones, video game consoles, or laptops. You may also want to create a separate guest network for visitors to use while in your home. This can help protect your personal devices from unauthorized access and malware infections designed to spread across networks. Where to access these settings will depend on your router but are often found under the router's settings page. Routers rented from internet service providers may require settings changes to be made on their account page.

Place the router in the center of your home
Generally, the best place for your router is in a central location, away from thick walls and solid surfaces that can interfere with Wi-Fi coverage and speed. Positioning your router on a shelf or table will reduce the distance that the signal has to travel. Typically a good signal is viable within 150 feet from the access point.
-
It is recommended to limit your Wi-Fi signal coverage to within your home to reduce the risk that unauthorized parties beyond your home can gain access to your network.

These simple steps will help you create a more secure home network and help protect your data and internet-connected devices. If you have any questions about this or any other resource, please contact the NJCCIC at NJCCIC@cyber.nj.gov.
Additional Best Practices
- Keep hardware and software updated.
- Use anti-virus/anti-malware on devices, where available.
- Enable and configure a firewall on the network.
- Disable unneeded or unnecessary ports on the firewall.
- Employ email security best practices.
- Enhance security and privacy settings on social media accounts and internet of things devices.







