DDOS Attack Types and Mitigation Strategies
Advisory
Garden State Cyber Threat Highlight
Original Release Date: 11/5/2020
Over the past several months, the NJCCIC noted a significant uptick in the number of distributed denial-of-service (DDOS) attacks in which thousands of malware-infected systems are used to flood organizations’ networks, thereby preventing or impairing the authorized use of the targeted networks, systems, or applications. In some instances, these DDOS attacks have resulted in organizations being unable to carry out critical business functions.
Since the outbreak of COVID-19, many organizations have shifted to remote work. Businesses, schools, and even individuals have become more dependent on online services for all aspects of work and daily life. The NJCCIC has seen a corresponding increase in a wide variety of cyberattacks since March of this year, including COVID-related malspam campaigns and more sinister ransomware attacks. More recently, school systems have become the targets of DDOS attacks. At a time when many schools are operating remotely, DDOS attacks can render a school’s online resources inoperable and unavailable to students, teachers, and administrators. This recent uptick in DDOS attacks, however, is not limited to schools. Numerous private and public sector organizations have also been targeted by DDOS attackers.
The motivations for DDOS attacks vary. DDOS threats against e-commerce sites and online businesses is a common extortion tactic used by threat actors motivated by financial gain. DDOS attacks are also another tactic being used to compel prompt payment in ransomware cases; however, financial gain is not the only motivation. In some cases, hacktivism, cyber warfare, and revenge are the underlying motivations. Some sophisticated threat actors will carry out DDOS attacks against an organization to draw attention to the DDOS attack, while at the same time carrying out other attacks undetected. At the other end of the spectrum, DDOS attacks may be carried out as a prank, similar to pulling the fire alarm or phoning in a bomb threat to a school to get out of sitting for an exam. In some cases, DDOS attacks are self-inflicted or accidental due to a misconfiguration of a network device or system. Regardless of whether it is a business, a government agency, or a school, the threat of a DDOS attack adversely impacting your organization is real and growing. As such, it is imperative that organizations include DDOS attack prevention and recovery in their cybersecurity plans.
Types of Attacks
There are various types of DDOS attacks that can create havoc for targeted organizations. In this article, we organize the types of attacks into three groups: volumetric, protocol, and application attacks, while acknowledging that the distinction between the three categories is blurred. Oftentimes, attackers will employ all three categories at once in order to ensure their attacks are as disruptive as possible.
Volumetric Attacks
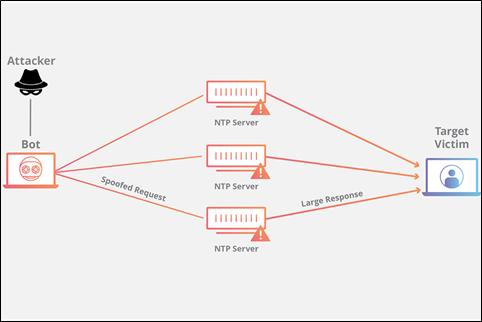
Volumetric DDOS attacks are the most common and most devastating. A volumetric attack overwhelms a network with massive amounts of network traffic thereby exhausting the target organization’s resources. In volumetric attacks, it is common for the attacker to employ numerous malware-infested systems - known as bots - to target an organization. User Datagram Protocol (UDP) and Internet Control Message Protocol (ICMP) floods are a common means of carrying out volumetric attacks. UDP and ICMP are connectionless protocols that allow for fast data transmission without integrity checks, which unfortunately makes them prime tools for attackers. Volumetric attacks also commonly use reflection and amplification techniques to overwhelm the target network/service. One type of UDP volumetric attack is a Network Time Protocol (NTP) reflection and amplification DDOS attack in which the attacker enlists thousands of bots to spoof a target system’s IP address while making NTP requests to legitimate NTP servers on the Internet. The result is a flood of traffic from the NTP servers to the targeted system, which overwhelmes it.
Image Source: Acunetix
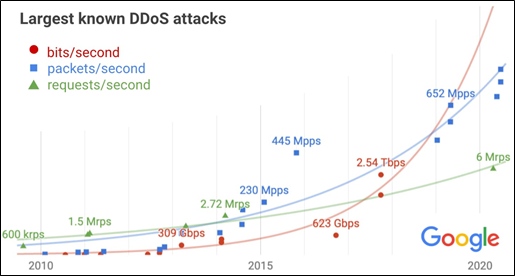
In volumetric attacks, the more bots and more servers enlisted to attack a given target ensures almost any network is overwhelmed. Google recently publicized that in 2017, it was subjected to the largest DDOS attack on record - 2.54Tbps. Its report on Exponential Growth in DDoS Attack Volumes paints a stark picture of the DDOS threat. As volumetric attacks saturate the bandwidth of the target network, they are typically measured in bits per second (bps).
Image Source: Google
Protocol Attacks
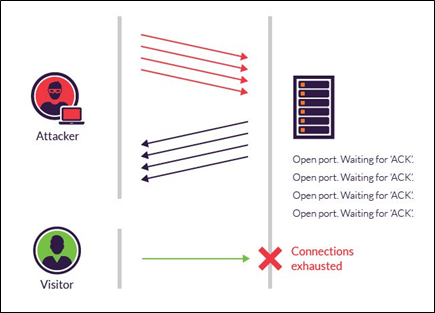
Protocol attacks are intended to consume all the resources of a given target network/service by sending it numerous successive malformed connection requests. A SYN flood is a common protocol attack. In a normal three-way handshake that establishes a connection between two computers, the client computer sends the host a SYN request. The host acknowledges the SYN request by sending back a SYN-ACK message, and then the client computer acknowledges the SYN-ACK by sending an ACK message to establish the connection with the host. In a SYN flood, numerous SYN packets are sent to every port on a targeted server using a spoofed IP address. The host responds with a SYN-ACK, but because the initial SYN packets were spoofed, there are no responses from the client. Eventually, the host computer’s ports will become overwhelmed with half-open connections and, as a result, legitimate connection requests will be denied. In addition to SYN floods, there are a number of other similar protocol attacks including Ping of Death, Smurf DDOS and more. Protocol attacks consume the processing resources of network equipment such as firewalls, load balancers, and servers and they are typically measured in packets per second (pps).
Image Source: Imperva
Application Layer Attacks
Application attacks target an organization’s web applications whereby the attacker sends numerous, seemingly legitimate, processing requests to the application. These attacks require the application to use CPU and memory resources until those resources are exhausted and the application cannot respond to any more requests. In an e-commerce site, processes to add an item to a shopping cart and to check out are computationally expensive. Attackers who target these application processes with numerous concurrent requests can exhaust the target system’s resources and crash the server. Application layer attacks are typically measured in requests per second (rps).
Preparation and Prevention
Any organization with an internet-facing service can become the target of a DDOS attack. As such, it is vital to have an incident response plan that accounts for DDOS attacks against your organization. The preparation phase of an incident response plan includes all the activities and controls that are implemented to prevent and prepare for a response to an attack. Oftentimes, the response to a DDOS attack includes working with your Internet Service Provider (ISP) or DDOS Mitigation Service Provider to assist in deflecting or scrubbing DDOS traffic aimed at your network. Establishing relationships with those providers ahead of any attack will help you prevent and quickly respond to attacks.
To mitigate the risk of an attack, organizations can take a number of actions. This list, while not comprehensive, will provide guidance in assessing and managing risk.
- Ensure your information security program includes capacity and performance planning policies and standards, such that your network, systems, and applications meet business requirements and are implemented in a manner that mitigate the risks of capacity and performance limitations.
- Conduct an inventory of internet-facing services and prioritize those that need protection from DDOS attacks.
- Ensure network capacity is appropriate. With the transition to remote work, organizations are using more bandwidth. Has your organization's bandwidth been increased to account for this expanded usage? Is the network hardware capable of handling increases in traffic?
- Limit the attack surface. Do not expose unnecessary ports or services to the internet that would make them potential targets. Most organizations have no need to expose NTP to the public internet. Drop that traffic at the router or have your ISP drop it upstream from your network. Similarly, drop or limit the bandwidth allocated to other risky protocols if there is no legitimate business need. Some risky protocols for consideration include Chargen, SMB, ICMP, SSDP, rpcBind, Ripv1, CLDAP, etc.
- Apply software and firmware updates and ensure security patches are applied in a timely manner on all network equipment and servers.
- Implement secure coding practices to minimize risks and to ensure the application’s components perform efficiently.
- Use multiple ISPs to provide redundancy and/or distribute the load. Some organizations use one ISP for their public-facing websites and services, and a different ISP for VPN and other internal business functions.
- As noted above, engage with your ISP ahead of time to establish an understanding of what protections and remediation help they can provide.
- Consider contracting with a DDOS mitigation service provider that monitors and automatically responds to attacks against your resources. When engaging such services, ensure you have a full understanding of their service level agreement that includes detection thresholds and time to mitigation.
Understand The Threat
DDOS attacks can be conducted with relative ease. There is virtually no technical competency necessary, only a motive. Your small business or school may not be target #1 for nation state actors; however, a disgruntled former employee, competitor, or student can initiate an attack with little resources. There are DDOS-for-hire services that utilize bot armies to conduct DDOS attacks against a target. The cost for these hires is usually calculated based on the amount and duration of traffic sent to a target. While DDOS attacks are illegal, these DDOS-for-hire services often advertise themselves online as booters or stressers that can be used to test your network’s resilience. The problem is that these services rarely check if you have authorization to conduct such stress tests. As such, almost anyone can anonymously hire these services to attack any target of their choosing.
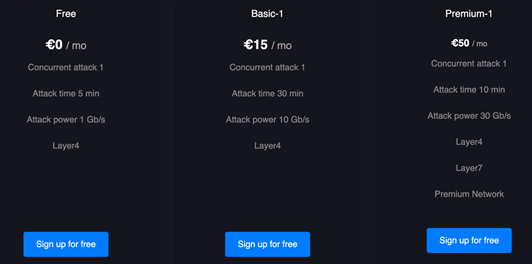
Screenshot of DDOS-for-Hire website
In the above screenshot, this stresser site requires the user to sign up for free with a username and password; however, other sites are completely anonymous – just insert the target IP, port, and duration and click the Launch button.
With the ease that DDOS attacks can be launched, organizations should expect to be targeted and to implement controls and a response plan to minimize the impact.
Additional Resources
DHS CISA – DDOS Attack Quick Guide